

Signal » Signal-desktop : Security Vulnerabilities
Switch to https://HomeBrowse :
VendorsProductsVulnerabilities By DateVulnerabilities By TypeReports :
CVSS Score ReportCVSS Signal desktop app vulnerability DistributionSearch :
Vendor SearchProduct SearchVersion SearchVulnerability SearchBy Microsoft ReferencesTop 50 :
VendorsVendor Cvss ScoresProductsProduct Cvss Signal desktop app vulnerability :
Microsoft BulletinsBugtraq EntriesCWE DefinitionsAbout & ContactFeedbackCVE HelpFAQArticlesExternal Links :
NVD WebsiteCWE Web Site
Copy ResultsDownload Results
| # | CVE ID | CWE ID | # of Exploits | Vulnerability Type(s) | Publish Date | Update Date | Score | Gained Access Level | Access | Complexity | Authentication | Conf. | Integ. | Avail. | |||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | CVE-2019-9970 | 2019-03-24 | 2022-04-07 | 4.3 | None | Remote | Medium | Not required | None | Partial | None | ||||||||
| Open Whisper Signal (aka Signal-Desktop) through 1.23.1 and the Signal Private Messenger application through 4.35.3 for Android are vulnerable to an IDN homograph attack when displaying messages containing URLs. This occurs because the application produces a clickable link even if (for example) Latin and Cyrillic characters exist in the same domain name, and the available font has an identical representation of characters from different alphabets. | |||||||||||||||||||
| 2 | CVE-2018-14023 | 200 | +Info | 2018-08-20 | 2018-10-15 | 2.1 | None | Local | Low | Not required | Partial | None | None | ||||||
| Open Whisper Signal (aka Signal-Desktop) before 1.15.0-beta.10 allows information leakage. | |||||||||||||||||||
| 3 | CVE-2018-11101 | 79 | Exec Code XSS File Inclusion | 2018-05-17 | 2018-06-19 | 4.3 | None | Remote | Medium | Not required | None | Partial | None | ||||||
| Open Whisper Signal (aka Signal-Desktop) through 1.10.1 allows XSS via a resource location specified in an attribute of a SCRIPT, IFRAME, or IMG element, leading to JavaScript execution after a reply, a different vulnerability than CVE-2018-10994. The attacker needs to send HTML code directly as a message, and then reply to that message to trigger this vulnerability. The Signal desktop app vulnerability software fails to sanitize specific HTML elements that can be used to inject HTML code into remote chat windows when replying to an HTML message. Specifically the IMG and IFRAME elements can be used to include remote or local resources. For example, the use of an IFRAME element enables full code execution, allowing signal desktop app vulnerability attacker to download/upload files, information, etc. The SCRIPT element was also found to be injectable. On the Windows operating signal desktop app vulnerability, the CSP fails to prevent remote inclusion of resources via the SMB protocol. In this case, remote execution of JavaScript can be achieved by referencing the script on an SMB share within an IFRAME element, for example: <IFRAME src=\\DESKTOP-XXXXX\Temp\test.html> and then replying to it. The included JavaScript code is then executed automatically, without any interaction needed from the user. The vulnerability can be triggered in the Signal-Desktop client by sending a specially crafted message and then replying to it with any text or content in the reply (it doesn't matter). | |||||||||||||||||||
| 4 | CVE-2018-10994 | 79 | XSS | 2018-05-14 | 2018-06-18 | 4.3 | None | Remote | Medium | Not required | None | Partial | None | ||||||
| js/views/message_view.js in Open Whisper Signal (aka Signal-Desktop) before 1.10.1 allows XSS via a URL. | |||||||||||||||||||
Total number of vulnerabilities : 4 Page : 1 (This Page)
Signal : Security Vulnerabilities
Switch to https://HomeBrowse :
VendorsProductsVulnerabilities By DateVulnerabilities By TypeReports :
CVSS Score ReportCVSS Score DistributionSearch :
Vendor SearchProduct SearchVersion SearchVulnerability SearchBy Microsoft ReferencesTop 50 :
VendorsVendor Cvss ScoresProductsProduct Cvss ScoresVersionsOther :
Microsoft BulletinsBugtraq EntriesCWE DefinitionsAbout & ContactFeedbackCVE HelpFAQArticlesExternal Links :
NVD WebsiteCWE Web Site
Copy ResultsDownload Results
| # | CVE ID | CWE ID | # of Exploits | Vulnerability Type(s) | Publish Date | Update Date | Score | Gained Access Level | Access | Complexity | Authentication | Conf. | Integ. | Avail, signal desktop app vulnerability. | |||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | CVE-2022-28345 | 74 | 2022-04-15 | 2022-04-26 | 5.0 | None | Remote | Low | Not required | None | Partial | None | |||||||
| The Signal app before 5.34 for iOS allows URI spoofing via RTLO injection. It incorrectly renders RTLO encoded URLs beginning with a non-breaking space, when there is a hash character in the URL. This technique allows a remote unauthenticated attacker to send legitimate looking links, appearing to be any website URL, by abusing the non-http/non-https automatic rendering of URLs, signal desktop app vulnerability. An attacker can spoof, for example, example.com, and masquerade any URL with a malicious destination. An attacker requires a subdomain such as gepj, txt, fdp, or xcod, which would appear backwards as jpeg, txt, signal desktop app vulnerability, pdf, and docx respectively. | |||||||||||||||||||
| 2 | CVE-2020-5753 | 670 | 2020-05-20 | 2022-04-07 | 5.0 | None | Remote | Low | Not required | Partial | None | None | |||||||
| Signal Private Messenger Android v4.59.0 and up and iOS v3.8.1.5 and up allows a remote non-contact to ring a victim's Signal phone and disclose currently used DNS server due to ICE Candidate handling before call is answered or declined. | |||||||||||||||||||
| 3 | CVE-2019-17192 | 670 | DoS | 2019-10-05 | 2022-04-07 | 7.5 | None | Remote | Low | Not required | Partial | Partial | Partial | ||||||
| ** DISPUTED ** The WebRTC component in the Signal Private Messenger application through 4.47.7 for Android processes videoconferencing RTP packets before a callee chooses to answer a call, which might make it easier for remote attackers to cause a denial of service or possibly have unspecified other impact via malformed packets. NOTE: the vendor plans to continue this behavior for performance reasons unless a WebRTC design change occurs. | |||||||||||||||||||
| 4 | CVE-2019-17191 | 20 | 2019-10-05 | 2021-07-21 | 5.0 | None | Remote | Low | Not required | Partial | None | None | |||||||
| The Signal Private Messenger application before 4.47.7 for Android allows a caller to force a call to be answered, without callee user interaction, via a connect message. The existence of the call is noticeable to the callee; however, the audio channel may be open before the callee can block eavesdropping. | |||||||||||||||||||
| 5 | CVE-2019-9970 | 2019-03-24 | 2022-04-07 | 4.3 | None | Remote | Medium | Not required | None | Partial | None | ||||||||
| Open Whisper Signal (aka Signal-Desktop) through 1.23.1 and the Signal Private Messenger application through 4.35.3 for Android are vulnerable to an IDN homograph attack when displaying messages containing URLs. This occurs because the application produces a clickable link even if (for example) Latin and Cyrillic characters exist in the same domain name, and the available font has an identical representation of characters from different alphabets. | |||||||||||||||||||
| 6 | CVE-2018-16132 | 400 | 2018-08-29 | 2018-11-08 | 7.8 | None | Remote | Low | Not required | None | None | Complete | |||||||
| The image rendering component (createGenericPreview) of the Open Whisper Signal app through 2.29.0 for iOS fails to check for unreasonably large images before manipulating received images. This allows for a large image sent to a user to exhaust all available memory when the image is displayed, resulting in a forced restart of the device. | |||||||||||||||||||
| 7 | CVE-2018-14023 | 200 | +Info | 2018-08-20 | 2018-10-15 | 2.1 | None | Local | Low | Not required | Partial | None | None | ||||||
| Open Whisper Signal (aka Signal-Desktop) before 1.15.0-beta.10 allows information leakage. | |||||||||||||||||||
| 8 | CVE-2018-11101 | 79 | Exec Code XSS File Inclusion | 2018-05-17 | 2018-06-19 | 4.3 | None | Remote | Medium | Not required | None | Partial | None | ||||||
| Open Whisper Signal (aka Signal-Desktop) through 1.10.1 allows XSS via a resource location specified in an attribute of a SCRIPT, IFRAME, or IMG element, leading to JavaScript execution after a reply, a different vulnerability than CVE-2018-10994. The attacker needs to send HTML code directly as a message, and then reply to that message to trigger this vulnerability. The Signal-Desktop software fails to sanitize specific HTML elements that can be used to inject HTML code into remote chat windows when replying to an HTML message. Specifically the IMG and IFRAME elements can be used to include remote or local resources. For example, the use of an IFRAME element enables full code execution, allowing an attacker to download/upload files, information, etc. The SCRIPT element was also found to be injectable, signal desktop app vulnerability. On the Windows operating system, the CSP fails to prevent remote inclusion of resources via the SMB protocol. In this case, remote execution of JavaScript can be achieved by referencing the script on an SMB share within an IFRAME element, for example: <IFRAME src=\\DESKTOP-XXXXX\Temp\test.html> and then replying to it. The included JavaScript code is then executed automatically, without any interaction needed from the user. The vulnerability can be triggered in the Signal-Desktop client by sending a specially crafted message and then replying to it with any text or content in the reply (it doesn't matter). | |||||||||||||||||||
| 9 | CVE-2018-10994 | 79 | XSS | 2018-05-14 | 2018-06-18 | 4.3 | None | Remote | Medium | Not required | None | Partial | None | ||||||
| js/views/message_view.js in Open Whisper Signal (aka Signal-Desktop) before 1.10.1 allows XSS via a URL. | |||||||||||||||||||
| 10 | CVE-2018-9840 | Bypass | 2018-04-10 | 2019-10-03 | 4.6 | None | Local | Low | Not required | Partial | Partial | Partial | |||||||
| The Open Whisper Signal app before 2.23.2 for iOS allows physically proximate attackers to bypass the screen locker feature via certain rapid sequences of actions that include app opening, clicking on cancel, and using the home button. | |||||||||||||||||||
| 11 | CVE-2018-3988 | 200 | +Info | 2018-12-10 | 2022-04-19 | 1.9 | None | Local | Medium | Not required | Partial | None | None | ||||||
| Signal Messenger for Android 4.24.8 may expose private information when using "disappearing messages." If a user uses the photo feature available in the "attach file" menu, then Signal will leave the picture in its own cache directory, which is available to any application on the system. | |||||||||||||||||||
Total number of vulnerabilities : 11 Page : 1 (This Page)
Another severe flaw in Signal desktop app lets hackers steal your chats in plaintext

Discovered Monday by the same team of security researchers, the newly discovered vulnerability poses the same threat as the previous one, allowing remote attackers to inject malicious code on the recipients' Signal desktop app just by sending them a message—without requiring any user interaction.

Signal desktop app vulnerability understand more about the first code injection vulnerability (CVE-2018-10994), you can read our previous article covering how researchers find the Signal flaw and how it works.
The only difference between the two is that the previous flaw resides in the function that handles links shared in the chat, whereas the new vulnerability (CVE-2018-11101) exists in a different function that handles the validation of quoted messages, i.e., quoting a previous message in a reply.
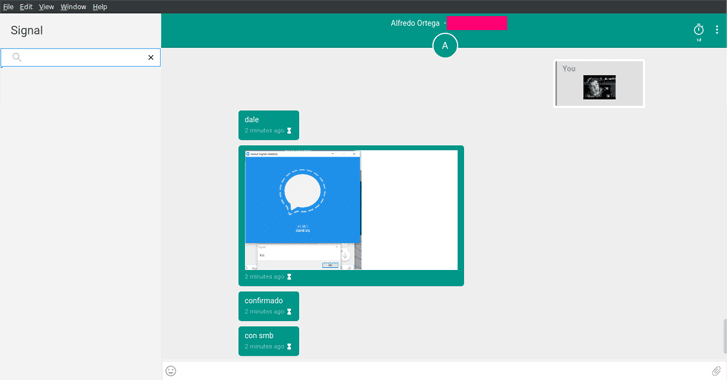
If the victim receives this quoted message containing the malicious payload on its vulnerable Signal desktop app, it will automatically execute the payload, without requiring any user interaction.
Exploiting Signal Code Injection to Steal Plaintext Chats
Until now the proof-of-concept payloads used to demonstrate code injection vulnerabilities in Signal were limited to embedding an HTML iFrame, or image/video/audio tags onto the victim's desktop app.
However, researchers have now managed to craft a new PoC exploit that could allow remote attackers to successfully steal all Signal conversations of the victims in the plaintext just by sending them a message.

This hack literally defeats the purpose of an end-to-end encrypted messaging app, allowing remote attackers to easily get the hold on users' plain-text conversations without breaking the encryption.
Attackers Could Possibly Steal Windows Password As Well
What's worse?
In their blog post, the researchers also indicated that an attacker could even include files from a remote SMB share using an HTML iFrame, which can be abused to steal NTLMv2 hashed password for Windows users.
"In the Windows operative system, the CSP fails to prevent remote inclusion of resources via the SMB protocol. In this case, remote execution of JavaScript can be achieved by referencing the script in an SMB share as the source of an iframe tag, for example: <iframe src=\\DESKTOP-XXXXX\Temp\test.html> and then replying to it," the researchers explain.Though they haven't claimed anything about this form of attack, I speculate that if an attacker can exploit code injection to force Windows OS signal desktop app vulnerability initiate an automatic authentication with the attacker-controlled SMB server using single sign-on, it would eventually hand over victim's username, and NTLMv2 hashed password to the attackers, potentially allowing them to gain access to the victim's system.
We have seen how the same attack technique was recently exploited using a vulnerability in Microsoft Outlook, disclosed last month.
I can not verify this claim at this moment, but we are in contact with few security researchers to confirm this.
Researchers—Iván Ariel Barrera Oro, Alfredo Ortega, signal desktop app vulnerability, Juliano Rizzo, and Matt Bryant—responsibly reported the vulnerability to Signal, and its developers have patched the vulnerability with the release of Signal desktop version 1.11.0 for Windows, macOS, and Linux users.
However, The Hacker News has learned that Signal developers had already identified this issue as part of a comprehensive fix to the first vulnerability before the researchers found it and reported them.
Signal app has an auto-update mechanism, so most users must have the update already installed, signal desktop app vulnerability. You can read this guide to ensure if you are running updated version of Signal.
And if you don't, you should immediately update your Signal for desktop as soon as possible, since now the vulnerability poses a severe risk of getting your secret conversations exposed in plaintext to attackers and further severe consequences.


Exploiting vulnerabilities in Cellebrite UFED and Physical Analyzer from an app's perspective
Cellebrite makes software to automate physically extracting and indexing data from mobile devices. They exist within the grey – where enterprise branding joins together with the larcenous to be called “digital intelligence.” Their customer list has included authoritarian regimes in Belarus, Russia, Venezuela, and China; death squads in Bangladesh; military juntas in Myanmar; and those seeking to abuse and oppress in Turkey, UAE, and elsewhere. A few months ago, they announced that they added Signal support to their software.
Their products have often been linked to the PowerBuilder For Windows of imprisoned journalists and activists around the world, but less has been written about what their software actually does or how it works. Let’s take a closer look, signal desktop app vulnerability. In particular, their software is often associated with bypassing security, so let’s take some time to examine the security of their own software.
The background
First off, anything involving Cellebrite starts with someone else physically holding your device in their hands. Cellebrite does not do any kind of data interception or remote surveillance. They produce two primary pieces of software (both for Windows): UFED and Physical Analyzer.
UFED creates a backup of your device onto the Windows machine running UFED (it is essentially a frontend to on Android and iTunes backup on iPhone, with some additional parsing). Once a backup has been created, Physical Analyzer then parses the files from the backup in order to display the data in browsable form.
When Cellebrite announced that they added Signal support to their software, all it really meant was that they had added support to Physical Analyzer for the file formats used by Signal. This enables Physical Analyzer to display the Signal data that was extracted from an unlocked device in the Cellebrite user’s physical possession.
One way to think about Cellebrite’s products is that if someone is physically holding your unlocked device in their hands, they could open whatever apps they would like and take screenshots of everything in them to save and go over later. Cellebrite essentially automates that process for someone holding your device in their hands.
The rite place at the Celleb…rite time
By a truly unbelievable coincidence, I was recently out for a walk when I saw a small package fall off a truck ahead of me. As I got closer, the dull enterprise typeface slowly came into focus: Cellebrite. Inside, we found the latest versions of the Cellebrite software, a hardware dongle designed to prevent piracy (tells you something about their customers I guess!), and a bizarrely large number of cable adapters.

The software
Anyone familiar with software security will immediately recognize that the primary task of Cellebrite’s software is to parse “untrusted” data from a wide variety of formats as used by many different apps. That is to say, the data Cellebrite’s software needs to extract and display is ultimately generated and controlled by the apps on the device, not a “trusted” source, so Cellebrite can’t make any assumptions about the “correctness” of the formatted data it is receiving. This is the space in which virtually all security vulnerabilities originate.
Since almost all of Cellebrite’s code exists to parse untrusted input that could be formatted in an unexpected way to exploit memory corruption or other vulnerabilities in the parsing software, one might expect Cellebrite to have been extremely cautious. Looking at both UFED and Physical Analyzer, though, we were surprised to find that very little care seems to have been given to Cellebrite’s own software security. Industry-standard exploit mitigation defenses are missing, and many opportunities for exploitation are present.
As just one example (unrelated to what follows), their software bundles FFmpeg DLLs that were built in 2012 and have not been updated since then. There have been over a hundred security updates in that time, none of which have been applied.
The exploits
Given the number of opportunities present, we found that it’s possible to execute arbitrary code on a Cellebrite machine simply by including a specially formatted but otherwise innocuous file in any app on a device that is subsequently plugged into Cellebrite and scanned. There are virtually no limits on the code that can be executed.
For example, by including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it’s possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, signal desktop app vulnerability, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures. This could even be done at random, signal desktop app vulnerability, and would seriously call the data integrity of Cellebrite’s reports into signal desktop app vulnerability app could contain such a file, signal desktop app vulnerability, and until Cellebrite is able to accurately repair all vulnerabilities in its software with extremely high confidence, signal desktop app vulnerability, the only remedy a Cellebrite user has is to not scan devices. Cellebrite could reduce the risk to their users by updating their software to stop scanning apps it considers high risk for these types of data integrity problems, but even that is no guarantee.
We are of course willing to responsibly disclose the specific vulnerabilities we know about to Cellebrite if they do the same for all the vulnerabilities they use in their physical extraction and other services to their respective vendors, now and in the future.
Below is a sample video of an exploit for UFED (similar exploits exist for Physical Analyzer). In the video, UFED hits a file that executes arbitrary code on the Cellebrite machine, signal desktop app vulnerability. This exploit payload uses the MessageBox Windows API to display a dialog with a message in it. This is for demonstration purposes; it’s possible to execute any code, signal desktop app vulnerability, and a real exploit payload would likely seek to undetectably alter previous reports, compromise signal desktop app vulnerability integrity of future reports (perhaps at random!), or exfiltrate data from the Cellebrite machine.
The copyright
Also of interest, the installer for Physical Analyzer contains two bundled MSI installer packages named and. These two MSI packages are digitally signed by Apple and appear to have been extracted from the Windows installer for iTunes version 12.9.0.167.
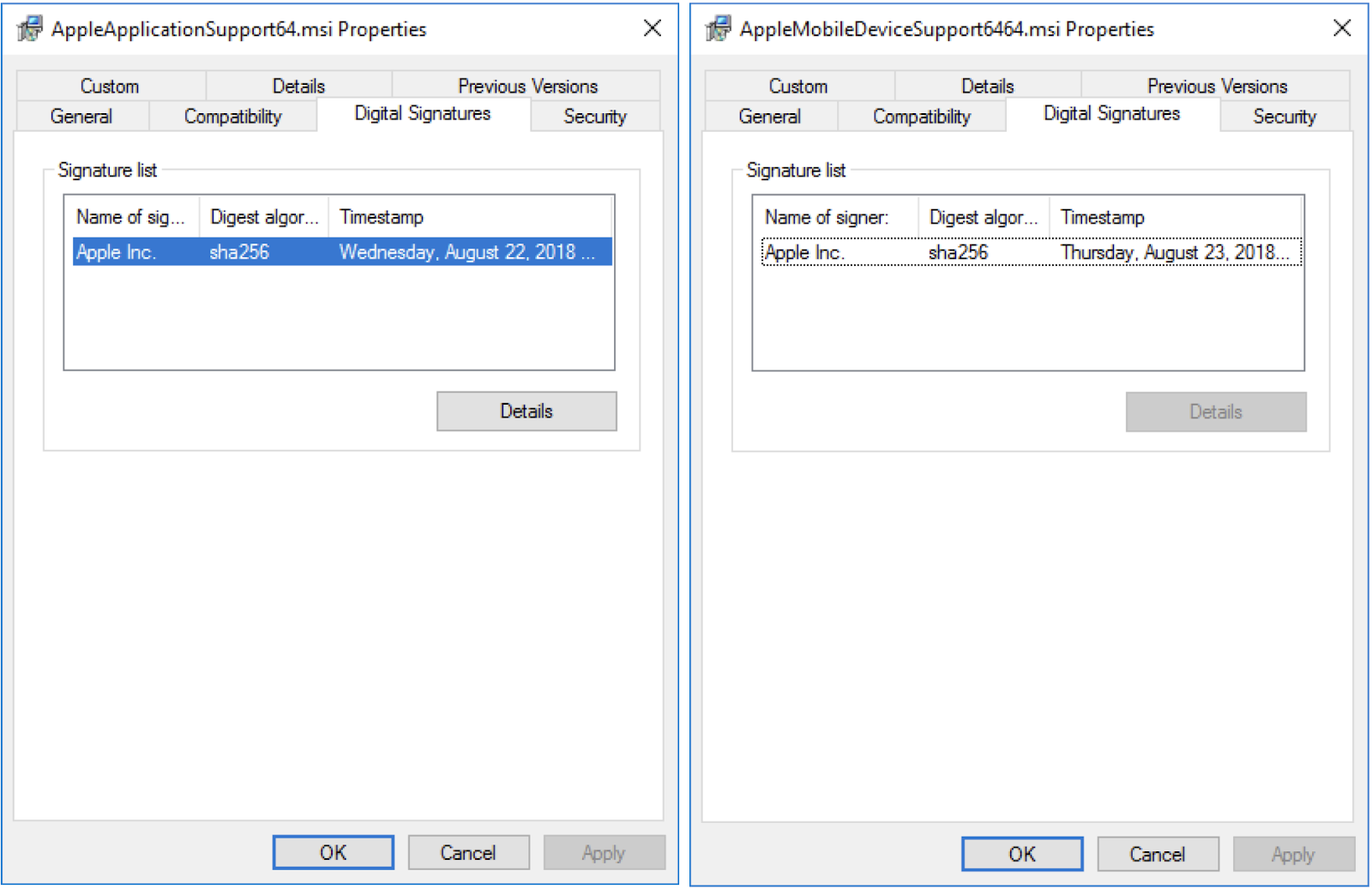
The Physical Analyzer setup program installs these MSI packages in. They contain DLLs implementing functionality that iTunes uses to interact with iOS devices.
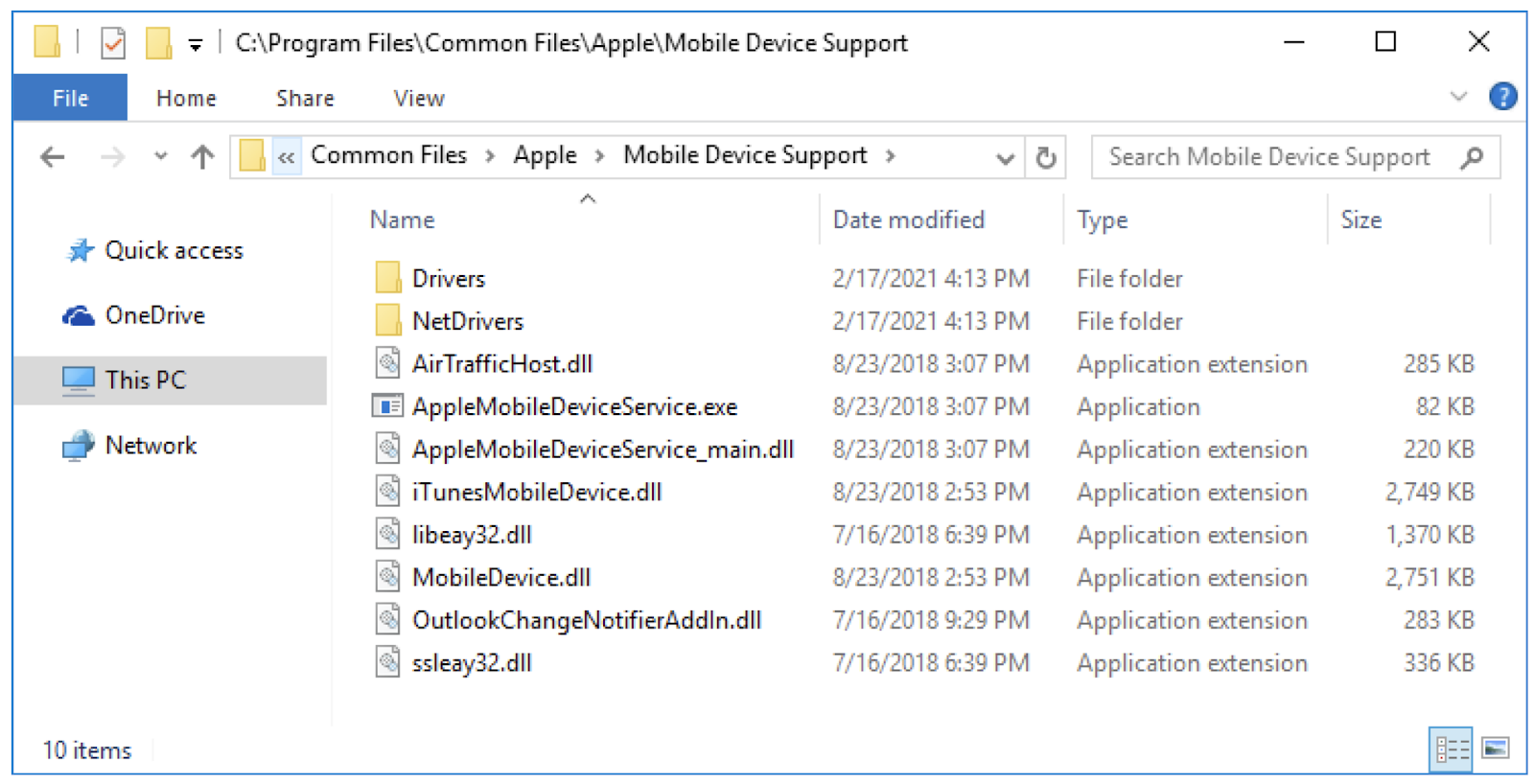
The Cellebrite iOS Advanced Logical tool loads these Apple DLLs and uses their functionality to extract data from iOS mobile devices. The screenshot below shows that the Apple DLLs are loaded in the process, which is the process name of the iOS Advanced Logical tool.
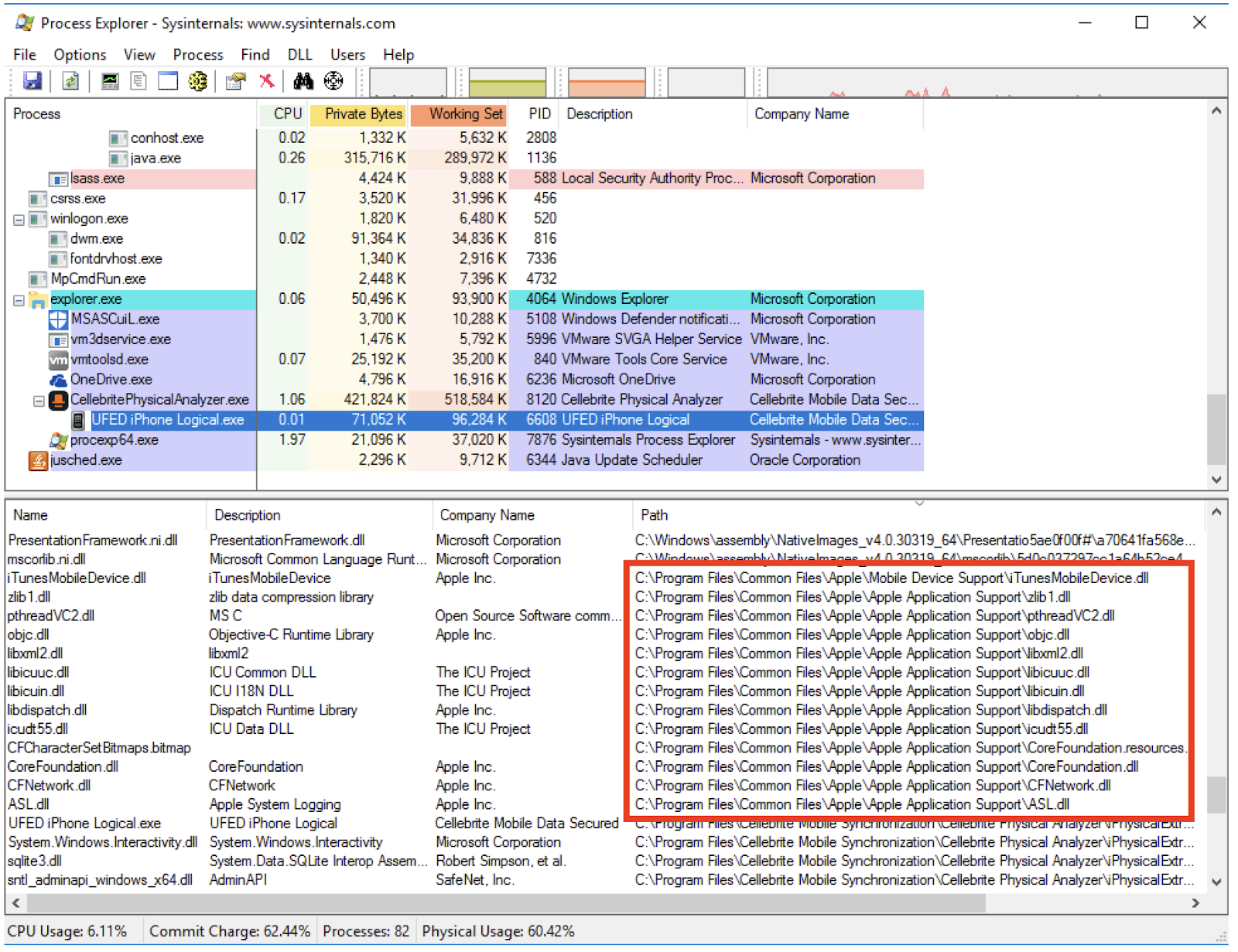
It seems unlikely to us that Apple has granted Cellebrite a license to redistribute and incorporate Apple DLLs in its own product, so this might present a legal risk for Cellebrite and its users.
The signal desktop app vulnerability unrelated
In completely unrelated news, upcoming versions of Signal will be periodically fetching files to place in app storage. These files are never used for anything inside Signal and never interact with Signal software or signal desktop app vulnerability, but they look nice, and aesthetics are important in software. Files will only be returned for accounts that have been active installs for some time already, and only probabilistically in low percentages based on phone number sharding. We have a few different versions of files that we CATIA V5R28 Crack + License Key Free Download 2021 are aesthetically pleasing, and will iterate through those slowly over time. There is no other significance to these files.
Tweet Facebook
Don't have Signal? Give it a try!
A bug discovered in the Signal application on Android enabled hackers to receive voice calls from the communicator – without the consent and awareness of the users. At the end of September, experts from Google’s Project Zero detected signal desktop app vulnerability error.

Signal is an encrypted application created for mobile devices by Open Whisper Systems. It supports both Android and iOS for mobile devices, there is also a desktop version of the program for Windows, Linux and macOS. Signal enables to make audio and video calls and to send multimedia messages – to individuals or groups.
Until now, the messenger was quite popular due to the “guaranteed” security of the users, signal desktop app vulnerability. Signal desktop app vulnerability Snowden himself promoted it. However, recent reports may undermine the authority of the application and weaken the trust of application users. As a specialist from Project Zero revealed, a bug in Signal enabled to turn on the microphone remotely without the victim’s knowledge.

As a result, cybercriminals could use the application to eavesdrop on specific people by only making a voice call. Without any user intervention, the audio call turned on the microphone of the callee device – before the conversation began.
Google experts say the vulnerability to hacker attacks involved voice calls in Signal. Video calls are not threatened by cyberattacks and are secured because it requires the callee to manually turn on the camera.
Creators of the messenger ensure that the error has been patched and recommend updating the application to version 4.47.7 as soon as possible.
The Next Web believes that the error in Signal’s software is similar to the vulnerability found in the FaceTime messenger from Apple. The latter also allowed hackers to eavesdrop on users with the use of incoming calls that enabled remote takeover of the mic.
AJ
Source: The Next Web
The Signal Electron App is not secure #1635
@scottnonnenberg I think it would be nice to hear a definitive answer from someone at OWS that the security issues in Electron mentioned by the OP have been remediated in Signal Desktop or have been reviewed thoroughly and found to be inapplicable. Signal desktop app vulnerability are a lot of assumptions being made and a lot of push-back that doesn't seem warranted and that hasn't been backed up with any tangible evidence.
Yes, I trust Moxie. Yes, OWS works very hard to make great crypto and secure software in general. That being said, none of those facts answer the question at hand and none of the replies here thus far have been enlightening: the vulnerabilities "may" have been fixed, some "may" not be applicable, OWS surely looked into it already, etc.
Well, if the vulnerabilities aren't relevant to Signal Desktop, at least briefly explain why for each one. If a vulnerability is relevant and was addressed, let us know it's been addressed; it shouldn't be difficult to point to the patch(es) addressing it. Attacking the OP for his alarmist title on this bug report or acting like the answers are all self-evident to everyone is not helpful or productive and undermines confidence.
Signal Desktop gatecrashed by web vulnerabilities
Two classic web flaws found in privacy-focused app within a week

Basic vulnerabilities were discovered by accident twice within Signal Desktop this week, raising questions about the app’s security.
A cross-site scripting (XSS) bug which allowed remote code execution (RCE) was first disclosed by researchers who posted a video of signal desktop app vulnerability successful exploit on Twitter.
The researchers – Ivan Ariel Barrera Oro, Alfredo Ortega, and Juliano Rizzo – stumbled across the flaw in Signal’s desktop app.
By sending a message, signal desktop app vulnerability, an attacker could have taken complete signal desktop app vulnerability over a user’s system.
Signal is widely-used due to its robust privacy guarantees, and while this bug (CVE-2018-10994) did not affect the encryption directly, by taking control over the system an attacker could still access encrypted messages.
Researcher Matthew Bryant decided to try his luck at figuring out how the team pulled off the exploit, he said.
He reproduced the problem by “guessing”, Bryant tweeted, as at that point no proof-of-concept or report had been published.
However, instead of figuring out the original issue Bryant had actually uncovered another flaw in Signal’s security.
His attack (CVE-2018-11101) was also able to employ RCE on the desktop app, but using a different method.
Bryant wrote in a blog post: “I began playing around with the Signal Desktop app trying to get arbitrary HTML markup to be evaluated but it didn’t appear to be straightforward.
“After trying a few different fields (name, signal desktop app vulnerability message, etc) I eventually found that if you created a message with HTML markup (say, <h1>Test</h1>), and you then did a Quoted Reply message to that message, the original markup would be evaluated as HTML!”
He added: “Upon reading the writeup I realized the researchers were just sending vanilla Signal messages which were being interpreted as HTML, and not the Quoted Replies that I had been using.
“As it turns out both were separate very similar vulnerabilities resulting in the same impact. Who could have guessed that?”
The original issue, discovered by the team of researchers, had already been patched, but didn’t protect against this new vulnerability.
Bryant disclosed his findings to Signal, who he said patched the issue “within hours”.
The original vulnerability was possibly already known about, the researchers noted, since it was due to be patched against in an April update, though this didn’t go ahead.
While Signal might be popular due to its robust cryptography and privacy for users, these findings were basic-level flaws open to be exploited by malicious actors with potentially serious consequences.
James Kettle, researcher at PortSwigger, said: “It's quite surprising to see such blatant vulnerabilities arising in security software of such pedigree.
“As well as signal desktop app vulnerability so obvious they were found by accident, the second one was introduced through unsafe use of a function called 'dangerouslySetInnerHTML' - hardly a subtle mistake.
“Everyone makes mistakes (us included) so it would be rash to judge Signal for this, but it makes me wonder if we'll be seeing more easy exploits in other apps in the future as Electron unleashes web vulnerabilities on unsuspecting desktop development teams.”
MobileRCEXSSVulnerabilities
WhatsAppFacebookRedditLinkedInEmail
 ';} ?>
';} ?>
0 Comments